BloodHound
Uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment.
Collectors
To gather additional information directly from ADExplorer for BloodHound, check ADExplorerSnapshot.py
Installation
Download newest release from Github.com
Apple macOS
The BloodHound binary is not signed, to still use it the following should be executed.
xattr -d com.apple.quarantine /Applications/BloodHound.appUsage
Bloodhound - Run ingestor on target domain joined system
.\SharpHound.exe CollectionMethod AllOr:
. .\SharpHound.ps1 /exeInvoke-BloodHound -CollectionMethod AllBloodhound - Remote ingestor
Please check BloodHound.py
AzureHound
Please check AzureHound
Examples
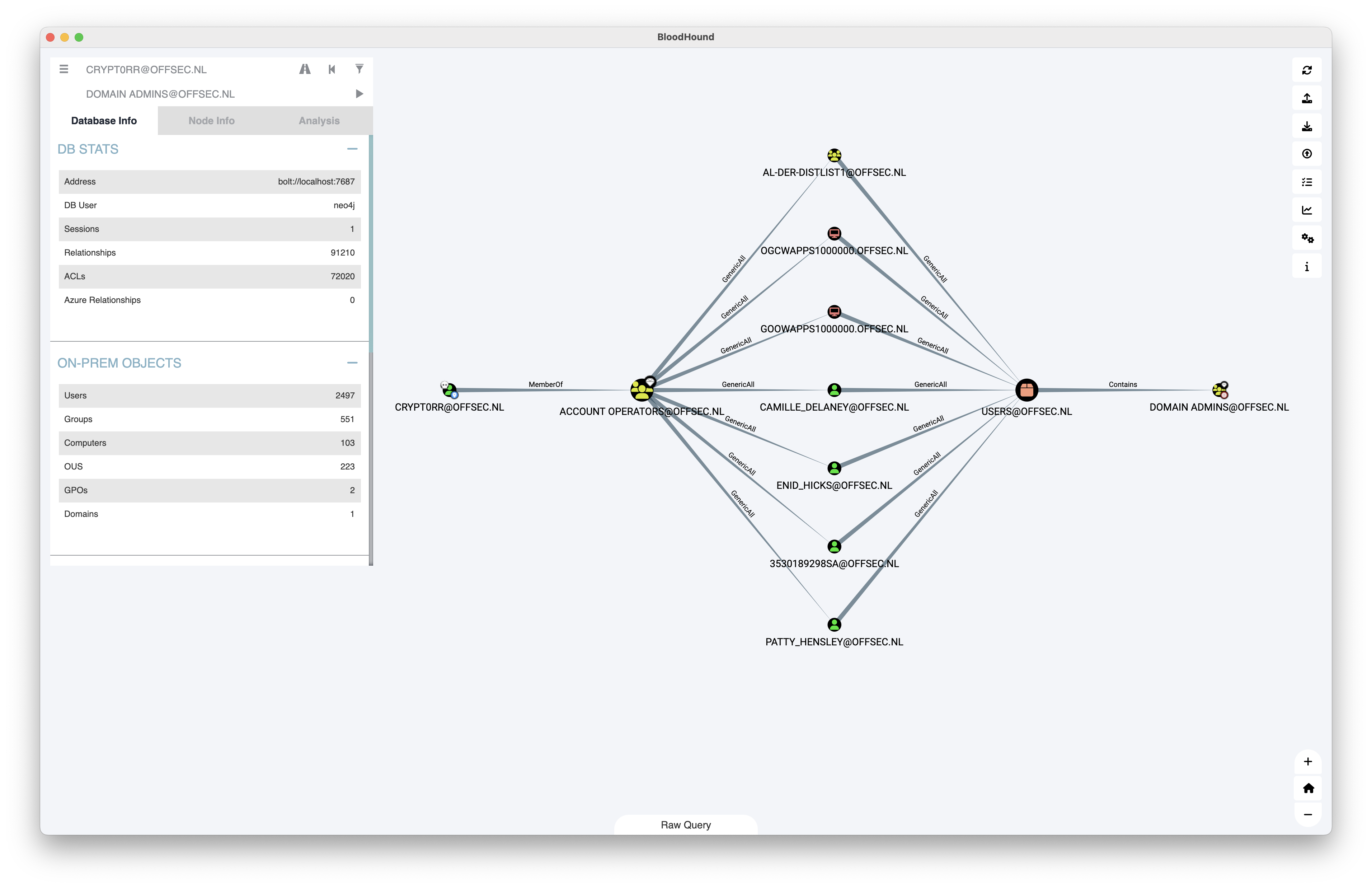
Example dataset
Dataset based on lab environment with BadBlood.
Statistics:
- Users: 2497
- Groups: 551
- Computers: 103
- OUS: 223
- GPOs: 2
- Domains: 1
Custom Queries
Linux
~/.config/bloodhound/customqueries.jsonmacOS
~/Library/Application Support/bloodhoundSome other custom queries:
- Github.com - mgeeky - Handy-BloodHound-Cypher-Queries
- Github.com - ly4k - Certipy
- Github.com - ZephrFish - Bloodhound-CustomQueries
- Github.com - CompassSecurity - BloodHoundQueries
- Github.com - Shutdownrepo - Exegol
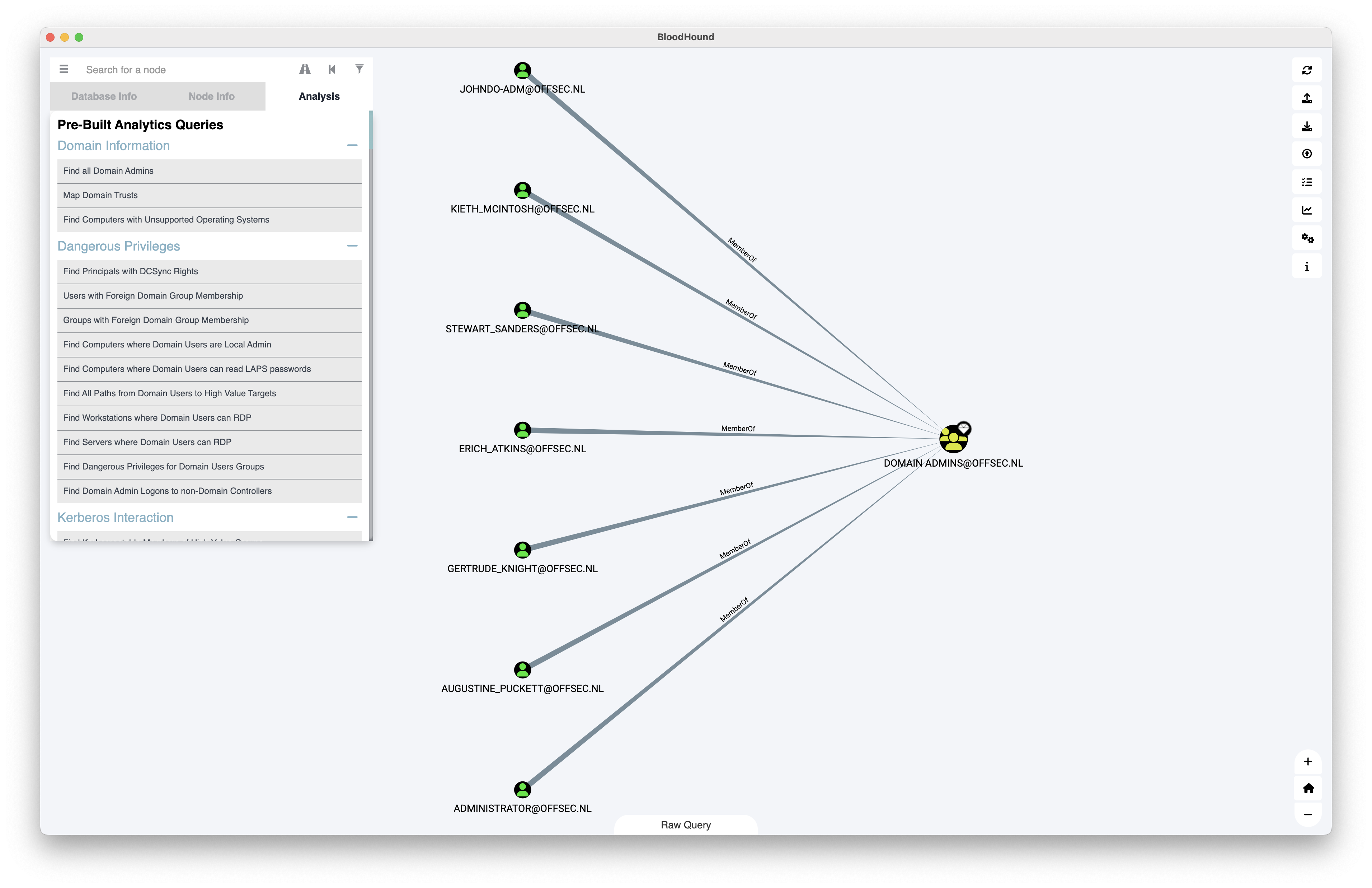
Filter users from json export Bloodhound
Filter domain admins
grep -E '"name":' da-export-bloodhound.json | cut -d '"' -f 4 | cut -d '@' -f1Excessive privileges allowing for shadow Domain Admins
ForceChangePassword – Ability to reset password of another user
GenericAll – Full control over an object (read/write)
GenericWrite – Update of any attributes of an object
WriteOwner – Assume ownership of an object
WriteDacl – Modify the DACL of an object
Self – Arbitrarily modify self- Infosecmatter.com - Top 16 Active Directory vulnerabilities
- iRed.team - Active Directory Kerberos Abuse
High privilege user groups
Administrators
Domain Admins
Enterprise Admins
Schema Admins
Account Operators
Server Operators
Backup OperatorsHelpfull Tools for BloodHound
Neo4j
Neo4j is usually used as database for BloodHound data. Please see neo4j for installation and multi-database usage.
CypherHound
Tool that can be used to interact with BloodHound collected data in the Neo4j database.
Please see CypherHound.
BloodHoundLoader
Tool that helps marking objects in the database, for example as owned or high value.
Please see BloodHoundLoader.